Introduction
This is the second part of the blog post, covering my second day at the conference. You can find the first part of the blog post here
Build your own Neural Network – with PHP!
Vítor Brandão, Noiselabs Consulting Ltd
An interesting session to start my second day, Vitor began by telling us that AI Machine Learning is all the hype these days and the trend is growing. He gave examples such as Netflix, Amazon recommendations etc. The session dove into the following topics and we got a tongue in cheek warning that there’d be some maths!
- Why are they called Neural Networks
- How do they learn
- Write one with PHP
- What the hell is Deep Learning?
He took us through how the brain’s neurons work and how they can be mapped into a mathematical function and the layers of a Neural Network.
The network can learn through supervised machine learning. Given a set of inputs, learn a function mapping to a known output so that we can accurately predict a new output from unseen inputs. The aim of the learning is to minimise the “wrongness” of the output.
Using PHP he then showed us it can be trained and to predict an XOR. The repository for the example can be found here.
Overall this was a really interesting session, though I definitely needed that morning’s coffee in order to stay focussed on the maths. Vitor is very knowledgeable on the subject and clearly enjoys it, his presenting style is really good and he checked in with the audience at times to ensure everyone was still with him. I really enjoyed getting a much better understanding of this topic.
Do PHP Frameworks still make Sense? Let’s go Frameworkless to focus on the Domain!
Damiano Petrungaro, HelloFresh
In this talk, Damiano shared his knowledge about how to keep using the framework as a tool and integrate DDD concepts to nail it.
He spoke about frameworks being an essential supporting structure and that new frameworks bring new approaches and push for innovation. Frameworks are important because they mean we do not need to reinvent the wheel and they define new standards. They also help with new joiners as they can onboard more easily since everything is well documented. However, using a framework has a cost and that cost can be high as the framework itself is a dependency.
Damiano gave a short introduction to the Frameworkless Movement, a group of developers who are interested in developing applications without frameworks. These developers do not actively hate frameworks but they perceive the misuse of frameworks as a lack of knowledge.
He also covered DDD, that the domain is not a dependency and that the focus should be on the domain and not the technology. Ask yourself what’s the problem you want to solve and begin designing a solution for that:
- Strategic Design
- Rules, boundaries and building a language you use when referring to terms.
- Communication is important, good communications means less noise.
- Bounded Context: dealing with large models and teams
- Tactical Design
- Value Objects
- Entities
- Aggregates
- Repositories
- Domain Events
- Domain Services
In conclusion, DDD will give us CQRS, Event Sourcing and Service Oriented Architecture. It can allow us to update the framework/library more easily and allow new joiners to learn the domain more easily with less breaking changes across the system.
This was an interesting session with some fairly obvious points that nonetheless are worth mentioning and covering again.
Migrating, with a Metal Background
Johann-Peter Hartmann, Mayflower GmbH
Having recently completed a migration of our datacentre systems (database, email and BI systems) over to the cloud (find more information on that over on LinkedIn), I was curious to attend this talk.
Johann-Peter spoke of the various options when moving from bare metal (your own servers) to the cloud. From “lift and shift” (rehosting) through to leveraging the Cloud services when you get there. He also spoke about the pros and cons of moving to the cloud and the cost of the services that can be offered by the provider.
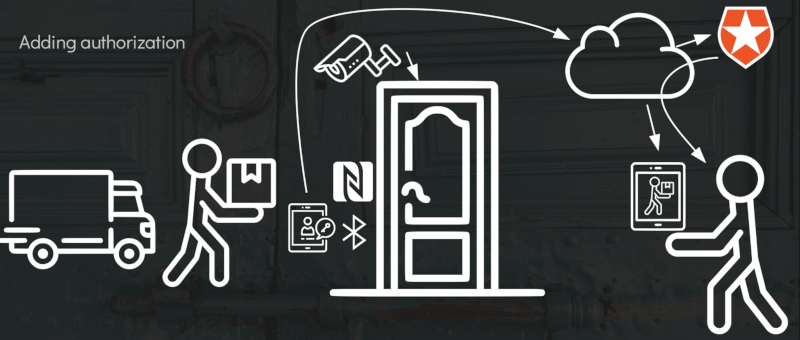
Opening Doors with JSON Web Tokens
Ben Dechrai - Auth0
A second talk by Ben Dechrai, this one was very hands on and was very interesting. The premise of the talk was to show us how to use JWTs to open doors. He began by bringing us back to the introduction of Amazon Key (a in-home service that allows Amazon to gain access to a Prime customer’s home at specified times). While this service seemed to solve a growing problem of the theft of packages left on doorsteps when the homeowners were not there (quite often experienced in the US), it also became apparent that its implementation had some vulnerabilities allowing unwelcome people to gain access.
Ben felt there was a better way to do this and he took us through a demo of how JSON Web Tokens could achieve this. He used a physical door with a connected Raspberry Pi controlling a door lock mechanism and leveraged Auth0 for authentication.
This was a really great talk and one to sit back and watch. Ben’s style is really impressive and entertaining, I think this was probably the session I enjoyed the most.
Security Champions? Introduce them in your Organisation
Ives Laaf (adesso as a service GmbH)
This talk asked the question, who should be responsible for security… the answer of course being everyone. While some companies have dedicated security teams, companies can also have Security Champions.
Anyone can be a Security Champion however such a person should know where things need to be improved and they should be a person who is driven to upgrade security.
Some of the benefits of having Security Champions for a company are:
- Scaling security through multiple teams
- Engaging “non-security” folks
- Best Practices can be defined
- Security relevant stories are prioritised in the backlog
OWASP have a Security Champion Playbook which contains 6 steps:
- Identify the Teams
- Is it one team for one product?
- What technology is used?
- Where is the code/documentation stored?
- What communication channels are used?
- Code review process?
- What is the Release calendar/cycle of the product
- Define the Role, such as, but not limited to:
- Measure the current security state among the team
- Define goals you plan to achieve in the mid-term
- Identify places where champions could help
- Verify security reviews
- Control best practices within the team
- Nominate Champions
- Get approval on all levels
- Communicate on all levels
- Otherwise you’ll hear: “I had no time for security”
- Setup Communication channels
- Define / Establish / Maintain
- Build a solid knowledge base, such as:
- Internal wiki as the main source
- Clearly defined roles and procedures
- Secure development best practices
- Checklists/Tools: SecurityRAT (Requirement Automation Tool). This is an OWASP tool with a checklist that can be used to talk to a team when they develop a feature so that they know the security topics to think about)
- Maintain Interest
- On all levels
- Workshops and Training
- Keeping them motivated
- Monthly security newsletters
- Visit security conferences
In Summary
This was a very enjoyable conference with excellent topics and speakers. Conferences are fantastic opportunities to hear other viewpoints and what’s going on outside your bubble. If you are considering going to one, I can fully recommend the IPC.